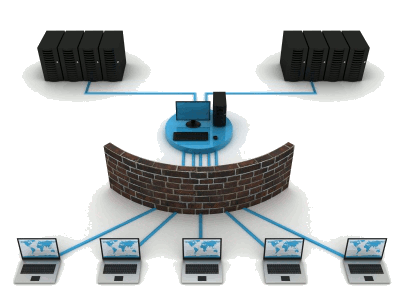
Network Security – Keep You Secure Online All The Time
End-user expectations, hyper-aggressive competition, speed-to-market demands and regulatory changes have forever changed the way service providers approach their customers. This – coupled with the complexities of network evolution, profitability pressures and commoditization of core business lines, such as voice and data – has forced providers to explore innovation in ways never before imagined.
CYK Network and System Integration Services supports both service provider and enterprise customers in their network and business evolution with a focus on these key transformation services:
- Network Design, Integration, Optimization and Migration expertise assist our customers in getting the most out of their network investments through network planning and design facilitation, network infrastructure optimization, multi-vendor network integration, and reliable migration to next generation infrastructure.
PCI compliance
Payment card industry (PCI) compliance is adherence to a set of specific security standards that were developed to protect card information during and after a financial transaction. PCI compliance is required by all card brands.
There are six main requirements for PCI compliance. The vendor must:
- Build and maintain a secure network
- Protect cardholder data
- Maintain a vulnerability management program
- Implement strong access control measures
- Regularly monitor and test networks
- Maintain an information security policy


HIPPA Compliance
HIPAA is an unusual law in that it makes a lot of recommendations (addressable items) and a few assertions (required items), but in the end it is up to each organization to determine for themselves what they need to do to be compliant. This creates a great deal of flexibility and also a great deal of uncertainty. In general, to be HIPAA-compliant, a web site must at a minimum ensure that all protected health information (ePHI):
- Transport Encryption: Is always encrypted as it is transmitted over the Internet
- Backup: Is never lost, i.e. should be backed up and can be recovered
- Authorization: Is only accessible by authorized personnel using unique, audited access controls
- Integrity: Is not tampered with or altered
- Storage Encryption: Should be encrypted when it is being stored or archived
- Disposal: Can be permanently disposed of when no longer needed
- Omnibus/HITECH: Is located on the web servers of a company with whom you have a HIPAA Business Associate Agreement (or it is hosted in house and those servers are properly secured per the HIPAA security rule requirements).
Web development
Web development is a broad term for the work involved in developing a web site for the Internet (World Wide Web) or an intranet (a private network). Web development can range from developing the simplest static single page of plain text to the most complex web-based internet applications, electronic businesses, and social network services. A more comprehensive list of tasks to which web development commonly refers, may include web engineering, web design, web content development, client liaison, client-side/server-side scripting, web server and network security configuration, and e-commerce development. Among web professionals, “web development” usually refers to the main non-design aspects of building web sites: writing markup and coding. Most recently Web development has come to mean the creation of content management systems or CMS. These CMS can be made from scratch, proprietary or open source. In broad terms the CMS acts as middleware between the database and the user through the browser. A principle benefit of a CMS is that it allows non-technical people to make changes to their web site without having technical knowledge.
Virtual Solutions Onsite DAS SAN NAS
Virtual machines allow you to run an operating system in a window on your desktop. Use them to run software made for other operating systems, experiment with different operating systems, and sandbox software.
There are several good free virtual machine programs, so setting up a virtual machine is easy. You’ll just need installation media for the operating system you want to install — this is free if you want to install Linux in a virtual machine, at least.
A virtual machine program is a computer program that creates a virtual computer system, complete with virtual hardware devices. This virtual computer “machine” runs as a process in a window on your current operating system. You can boot an operating system installer disc (or live CD) inside the virtual machine, and the operating system will be “tricked” into thinking it’s running on a real computer. It will install and run just as it would on a real, physical machine. Whenever you want to use the operating system, you can open the virtual machine program and use it in a window on your current desktop.
Cloud Solutions
Is the task of constantly upgrading your server, OS and applications costing you valuable time and resources, as well as draining your IT budget? Would you like to just simply offload not just the management of your systems, but your actual systems in Chicago themselves to another organization? Would you like to ensure your systems are hosted by an organization with skill in ensuring your systems are always up-to-date, secure and available 24/7?With Virtual Hosted Office “cloud computing” , your business will finally experience reduced downtime, eliminated costs of upgrades, and an increased level of security while running smoothly no matter what local disruptions occur in your office. We can host your entire IT infrastructure in the cloud, wholesale eliminating most if not all of your in-house IT management expenses — you ultimately will have access to all your systems from the Internet itself.

Onsite and Offsite private backups
The Cyk Network Managed Services team understands the importance of data security and HITECH/HIPAA compliance to keep our clients protected. We manage important security patches, e-mail and data encryptions, backups, disaster recovery planning and keep up with important HITECH changes.
- Secure Encryption on your offsite backup
- Keep as many backups as needed
- Email Alerts for your backup
- Monthly or Yearly Payment Plan
Altaro VM Backup
- No Upfront Costs
- Pay Based On Usage – Pay per VM per month, which means you pay only for what you use
- Recurring Revenue – Charge your customers a monthly recurring fee
- Central multi-tenant management – Monitor and manage all your customer installations through a single online management console
- Latest features – You will have access to the most current version of the Altaro VM Backup Unlimited Edition to use across your customers
- ‘Best Support in the IT industry’ – 50 second average call pick up, LIVE chat, speak directly with an expert, no tier 1 agents or gatekeepers
About CYK Network
Simplifying your technology, and your business.
Cyknetworks.com provides IT services to businesses in New York City and the New York metro area. Our staff has over 10 years of experience providing information technology services to business of all sizes. We specialize in network engineering, technical support, security, and most importantly, customer service. Our company builds lasting relationships by making businesses work better.
By outsourcing the management, maintenance and support of your business IT to Cyknetworks.com, you can finally take the stress out of using the technology your business counts on everyday. With a customized IT solution from our team of experts, you’ll finally begin to think of your technology as a strategic investment, rather than a constant drain on your time and resources.
Expert IT support from Cyknetworks.com takes the focus off your technology problems and puts it back on what really matters – your business.
Here’s why so many businesses depend on Cyknetworks.com for IT service and support:
• Our Microsoft Small Business Specialist Certification – recognizing our skill in delivering modern, reliable IT solutions
• Our Registered Microsoft Partner status – reserved for companies that demonstrate excellence in implementing Microsoft technologies
Discover why so many businesses are turning to cyknetworks.com for the best and brightest in IT support.
Trend Micro Small Business Store
Contact Us
Feel free to email us, phone us, smoke signal us, carrier pigeon us, or visit us. You can find us using our map (just scroll down a bit).
Company Info
 orders@cyknetworks.com
orders@cyknetworks.com 646-862-0184
646-862-0184 Brooklyn N.Y.
Brooklyn N.Y.
Have a question or comments? Click here




 646-862-0184
646-862-0184 Brooklyn N.Y.
Brooklyn N.Y.